WannaCry: 7 steps to protect yourself!
Our experts reverse engineered and analysed the code, our vulnerability analysis is published!
The story:
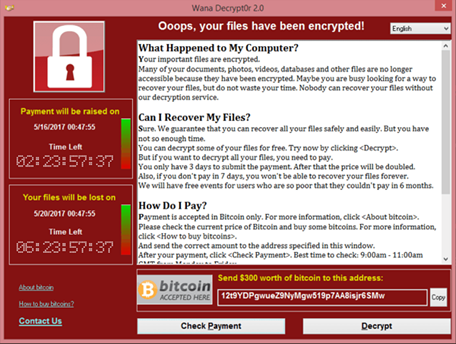
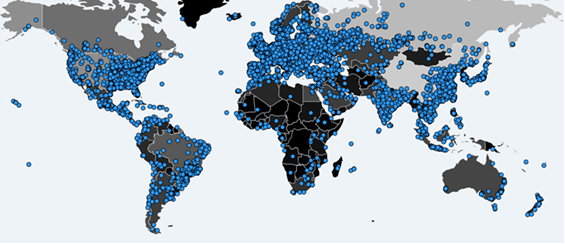
On Friday, 12 May 2017, the largest ransomware cyber-attack to date has been launched, called WannaCry,(or WannaCrypt, WanaCrypt0r 2.0, Wanna Decryptor) which by now infected more than 230.000 computers in 150 countries, demanding $300-$600 worth cryptocurrency called bitcoin.
Rumors say WannaCry uses the EternalBlue exploit, which was developed by the NSA to attack computers running Microsoft Windows operating systems. Microsoft released a patch to address the vulnerability in question for supported systems (Vista and up) on 14th March 2017, but this did not prevent the attack due to delays in applying security updates and a lack of support to legacy Windows versions (e.g. XP) still being in use by many. Shortly after the large scale attack, Microsoft decided to release a patch – even for these no longer supported versions.
Just after the exponential spread of the malicious software, a researcher (nick: MalwareTech) found a kill switch, – there was an unusual domain name in the code, which he registered – and this has slowed the spreading of WannaCry. The cat-and-mouse game kicked-off immediately: new variants of the malware appeared, implying new kill switch domain names that had to be registered.
7 steps to protect yourself:
Source: Mohit Kumar (Entrepreneur, Hacker, Speaker, Founder and CEO — The Hacker News and The Hackers Conference.)
- Update your systems: if you are using supported, but older Windows – install the update sor eventually upgrade it to Windows 10.
- If you are using unsupported versions: (including: Visa, XP, Server 2003, 2008) you need to apply an emergency patch released by Microsoft shortly after the outbreak. You can download it here.
- Disable SMBv1: by following these steps.
- Enable firewall: if it is already enabled, modify the configurations to block access to SMB ports. It operates on TCP ports 137, 139 and 445. UDP ports are 137 and 138.
- Update your anti-virus software: Virus definitions are already updated to protect against this threat.
- Backup: and backup regularly, create yourself a routine and keep your important files on an external storage that is not always connected to your PC.
- Phishing awareness: always perceive unsolicited documents you receive that they might bear such threats – and never click any link inside these documents until you can verify the source.
SCADEMY Secure Coding Academy courses teach your engineers how to code correctly to prevent bugs leading to similar infections; visit our course catalog to check our security courses. Get in touch!