Short story:
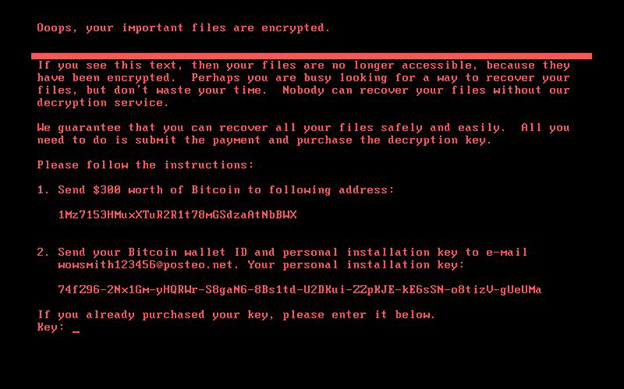
From June 27th another widespread ransomware attack is wreaking havoc around the world, utilizing a new variant of Petya (originally discovered in March 2016), dubbed NoPetya, Petna, PetrWap, Petra because of the differences in comparison of its earlier versions. The first incidents were reported from Ukraine, distributed through a software update mechanism built into an accounting program (M.E.Doc). From there, it has spread to Russia, Poland, France, the UK, Italy, Germany and the US too – among many others. It demands $300 worth of bitcoin cryptocurrency. Government, banks, state power utility, airport and even the radiation monitoring system at Chernobyl were hit, but also big companies such as Mondelez, Nivea, Mars, Rosneft, Merck, Moller-Maersk, WPP, DLA Piper and many more.
The malware is focused on lateral infiltration of a corporate network. Once it’s present on a machine, it first tries to infect other machines by copying itself onto them in three different ways:
- Using the EternalBlue exploit (just like WannaCry)
- Using the PsExec remote process execution tool – included in the payload – to run an infected executable on the target machine
- Using the Windows Management Instrumentation Command-line (WMIC) to run the infected executable on the target machine
Petya lockscreen (Source: Symantec)
Tips for organizations and individuals to defend against Petya
(Source: Paul Norris, TripWire; Balazs Kiss, Scademy)
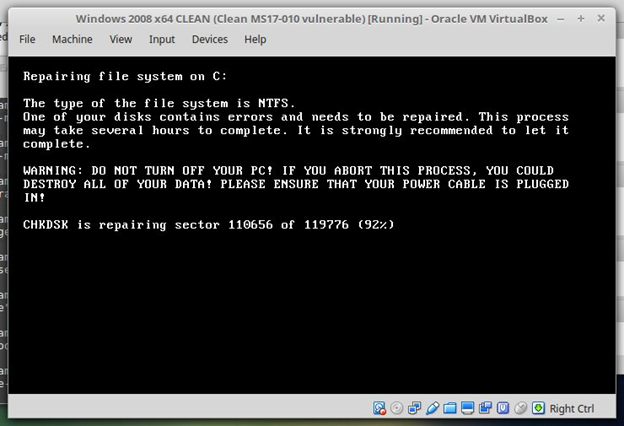
The malware needs administrator access to the local computer, and the file encryption can be prevented by either disabling Windows from rebooting if there is a crash or simply powering off when the encryption process starts. Petya encrypts the Master File Table – which is the index of where all the files are stored on a hard disk drive – in addition to the files themselves.
Prevention for organizations:
- Install the latest Microsoft patches, make sure MS17-010 is included
- If you do not use it, disable SMBv1 so the malware cannot use EternalBlue to spread across the network
- If you do not use them, disable administrative shares to prevent the other two infection methods from succeeding
- Update your anti-virus software as they are deploying updates to cover this particular malware as well
- Make sure you have a backup system in practice
- Instruct end-users to be alert when clicking links of opening attachments from unknown sources
- Restrict the local administration access to privileged users; avoid giving each of your users local admin access to all machines unless necessary to protect against the PsExec vector
- Educate end-users to write data only to the designated areas of the local hard disk to prevent data loss
- Disable automatic windows reboot on crash
Petya encryption routine (Source: HackerFantastic)
Measures for individual users:
- Make sure automatic updates are enabled on your operating system
- Install the latest anti-virus updates
- Consider setting up a standard user for day-to-day use instead of admin user on your computer and make sure you have enabled User Access Control
- Use cloud backup systems or an online storage provider to back-up and store your data
- Consider disabling automatic windows reboot on crash – here’s how
- Do not pay the ransom –payment distribution has been disabled, so you will not recover your files this way
We hope these measures can help you avoid or eventually mitigate the threat.
Stay safe!
Back